IMPLEMENTING SECURE ARCHITECTURE WITH RC3
CLIENT:
Worthworm, web-based pre-money valuation (PMV) system for early stage ventures seeking investment and angel investors.
CLIENT NEED:
Security and encryption of sensitive user information including business ideas, company specifics, personal data and the network.
SOLUTION:
Implementation of the Strong Authentication using StrongAuth KeyAppliance to achieve state-of-the-art encryption of the sensitive data and security of the user information.
Worthworm is a sophisticated and rigorous online system that analyzes more than 1100 parameters and over 4000 outputs to yield strong valuation data for entrepreneurs, early stage ventures and angel investors. It precisely calculates valuation based on the combination of valuation methods, incorporates proven industry outcomes of same-stage like companies, and develops a risk analysis profile assessing key business drivers that have the greatest impact on startup value.
Clients are required to answer an exhaustive questionnaire focused on the key valuation drivers of an early stage company. Answers are processed through the proprietary algorithm based on the Real Options technology to generate accurate valuation.
As a result, Worthworm produces credible pre-money valuation that clients can confidently present, pitch and defend during the meeting with potential investors.
CHALLENGE
Worthworm’s questionnaire is the basis for the valuation calculation. Clients have to answer questions about product differentiation, competitive advantage, current sales figures, management team, prior funding and risk factors.
Thus, protection and security of proprietary business ideas, company data, personal information and the network is of an extreme importance to Worthworm, and can potentially define the success of the application on the market.
Sensitive information provided by the customer required sophisticated security measures and data encryption comparable to those provided by the financial institutions.
Kanda Software faced the challenge to find cost-effective, but scalable solution for data encryption and key-management to provide Strong Authentication for the platform.
SOLUTION
KeyAppliance is an integrated solution for compliance to PCI-DSS, 201 CMR 17.00, HIPAA/HITECH, FISMA, the EU Directive and similar data-security regulations for the protection of sensitive data.
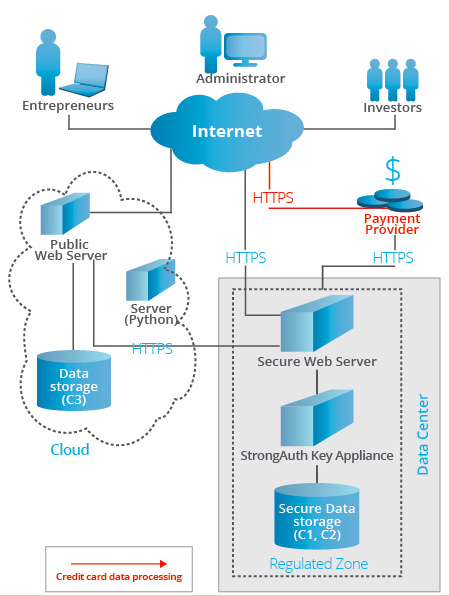
Adhering to RC3 allowed to efficiently distribute sensitive data across regulated zones, public clouds and servers. KeyAppliance was used to encrypt, tokenize and provide key-management in regulated zones within secure network perimeter. These zones are compliant with data security standards.
Following RC3 best practices for building applications Kanda team has classified Worthworm data into 3 categories
This design provided effective management of the existing and new data and conformity with the security standards for each data type. RC3 architecture also simplified communication between business units and IT.
Worthworm system was designed to adhere to Regulatory Compliant Cloud Computing to ensure maximum protection of the user information. According to RC3 specification the data was divided into 3 classes:
- Class 1: credit card, payment and purchase information.
- Class 2: user information, including personal details and e-mails, business information that consisted of venture and model names, questionnaire responses and any other business sensitive data.
- Class 3: non-sensitive information.
Class 1:data is processed and stored in regulated zones, within a secure network perimeter. They are compliant with applicable data-security regulations. Class 1 data is encrypted and tokenized. Class 2 data also undergoes encryption and tokenization. However, it is processed in secure, but not regulated zones.
StrongAuth KeyAppliance is used for encryption, decryption, search and deletion of the data stored in the system. Additional key-management automation capability allowed Worthworm to drastically reduce the number of requests to the web-service while in use.
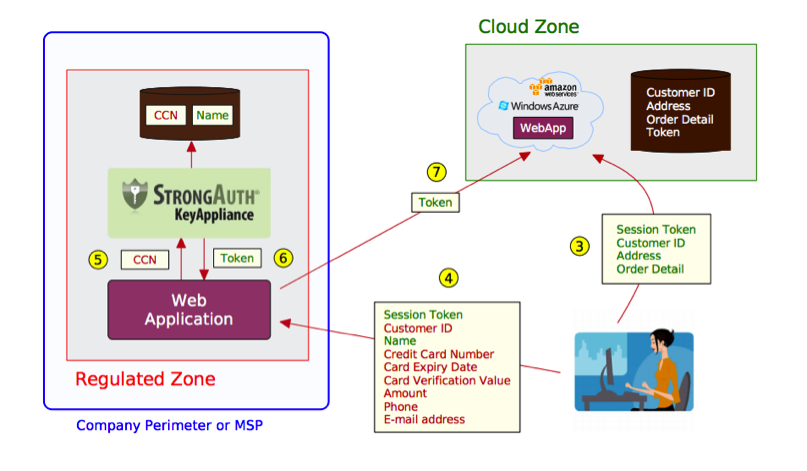
The data is encrypted before it is stored in the database and decryption process happens when the data needs to be sent to the user through Worthworm interface. This way Kanda Team ensured that no sensitive data is ever passed to or maintained on the user side.
KeyAppliance is also used for user authorization process. The user is authorized based on comparison of login credentials with the existing tokens in the system. The system searches for the similar token and, if found, grants access to the user. This method provides additional data security without system flexibility loss or any other additional restrictions on the user side. The password can be recovered any time via e-mail without decreasing security of the system and transparency to the end user.
Kanda has integrated KeyAppliance into Worthworm infrastructure using Spring Web Services that ensured additional flexibility.
SOLUTION BENEFITS
Implementing RC3 along with the StrongAuth KeyAppliance allowed Kanda Software and Worthworm teams to leverage cloud technologies and achieve lower implementation costs, faster time to market and scalability along with compliance to data security regulations.
In addition, KeyAppliance provided such benefits as:
- Key management automation including key-generation, escrow, recovery and access-control
- Data security compliance while leveraging public clouds for processing sensitive client information and transaction data
- Easy scalability
- NIST-approved encryption algorithms
- Integrated cryptographic hardware module with a true random number generator
- Secure and robust messaging services for data and key replication
About StroungAuth
StrongAuth, Inc. is a Silicon Valley-based company. Focused exclusively on enterprise key-management solutions, it has been building key-management infrastructures for the last decade. Its PKIAppliance, KeyAppliance and CryptoAppliance products are used to protect sensitive data in dozens of mission-critical environments around the world.